Thoughts on CPTC and CCDC

CTFs vs. Applied Cyber¶
These competitions are quite different from the typical cyber competitions most people participate in, like CTFs. They don't involve capturing flags or solving custom crypto challenges. Instead, they focus on enterprise-like scenarios with actual systems and services that real businesses use. This makes it a lot more interesting and challenging, as it requires you to interact with various configurations and services, all while under pressure.
CPTC (The Red Teaming One)¶
CPTC is quite different compared to CCDC, as the entire competition happens within a day. We had time to prepare things like scripts and tooling beforehand (which is also public to all other teams), but the actual competition is about 8 hours long. At the end of the simulated penetration test, you have until midnight to submit a detailed professional report of your findings and recommendations.
As you might guess, the report is a significant portion of the overall score. To put it bluntly, if you're not working on the report during the competition, you're going to get screwed over by the deadline. There's no feasible way to wake up early, travel to the competition, compete for 8 hours, debrief with competition organizers, go back home, and then write a large report in however many hours you have left. Here's the scoring breakdown:
| Category | Weight |
|---|---|
| Technical (Technical findings within the report) | 30% |
| Injects (Business-related tasks during the competition) | 40% |
| Report (Overall report structure, formatting, key areas) | 30% |
The Competition¶
The competition itself was something. We started with a delay due to some technical issues on the organizer's side. Beginning with some generic recon, running network topology scans, and service enumeration, we figured out what type of network we were dealing with as we were not given a schematic of the network beforehand. A tip for future teams: write some scripts beforehand to do this.
While dealing with the network, we also had to handle injects, aka random people busting into our conference room and either asking us questions (while playing dumb corporate) or giving us tasks to do. These tasks ranged from presentations on "radio emissions and RF attacks on airports" to writing a 3-page document on "how to disrupt airport operations." We had 2-3 of our 6 team members working on injects, while everyone else worked on pen-testing. We had a few funny moments, like corporate walking in a bit after we had accidentally crashed a service, which they noted in their grading feedback:

Other than the injects, it was fairly straightforward: look for low-hanging fruits like default credentials, misconfigurations, and outdated software. This can mainly be done with a bit of enumeration and CVE scans, so it's not too hard to get started in one direction. A harder part was trying not to break stuff while prying into the network.
Given this was my team's and my first time participating in something applied like this, we didn't know the technology stacks as well as we should have. Funny enough, we were given a whole AWS environment and some injects related to it, but nobody on our team knew anything about AWS, so we kinda just ignored it. During the second day, which was just for the debrief and awards ceremony, we were shown what commands they logged everyone using in the jump boxes:
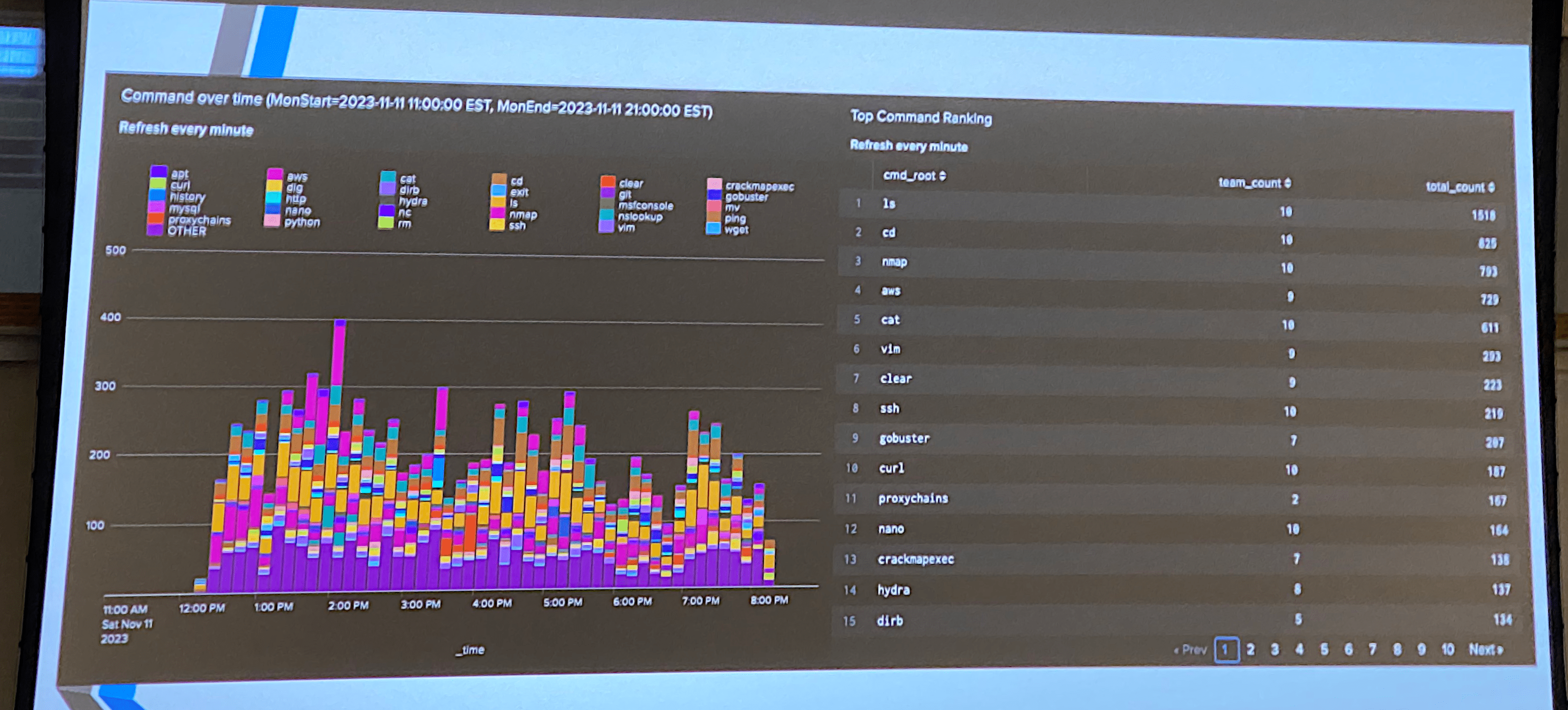
Final Thoughts¶
I think my immediate critique is that the competition is way too short. Unlike CCDC (which I'll talk about later), you only have 8 hours to do the pentest, then 6 hours to write a report, not considering things like travel time and breaks. It took our team about 2 hours to get to Stanford (where the competition took place) and 2 hours to get back. I can only imagine the teams that had to fly in, we all barely got any sleep.
Another thing to note is that the environment is pretty much static. There's not much dynamic stuff happening, and you're not allowed to be disruptive (which makes sense for a company doing a pentest), but it makes it boring. At most, you're having a bit of fun with msfconsole and throwing some exploits at boxes with CVEs to get root.
The competition itself is really business-focused (so many suits at finals). Even with executive-level presentations at modern companies, I think it's a bit too much. Also, the staying in character thing at all times just felt off. The organizers were the same people playing the roles, so half the time I was trying to figure out if it was OOC. It seems weird to get points taken off because you barged into our room while we were playing music and talking about random stuff.
Overall, it was fun to meet some of the other teams. We got to meet some friends from other schools, and it seemed like most people had fun. I had a pretty funny run-in with another team where someone asked me if we could ping the two subnets, and I said, "Yeah, all four are up." They gave me a weird, confused look, and asked what I meant by four subnets. Little did they know, apparently their team had missed two of the largest subnets on the network.

If I had to sum my advice up in a few points, it would be:
- Prepare tooling beforehand (mainly recon, enumeration, and whatnot)
- Get at least 3 people on injects
- Write the report as you go, make sure you have screenshots saved of everything
- Don't break stuff
- Play into the serious corporate role as weird as it may feel
CCDC (The Blue Teaming One)¶
Compared to CPTC, CCDC seems a lot larger in scale. The actual competition is divided into regional qualifiers, regionals, and then nationals. There were two qualifier opportunities, each running for about 8 hours, and the top teams from each qualifier moved on to regionals. Qualifiers were a bit different from regionals, as we were able to compete virtually from our school.
Qualifiers¶
The actual qualifiers were much more engaging. We had to defend a live network from an active threat (the red team), all while maintaining services and dealing with "customers." We had something like 13 boxes to manage, some being Linux, some being Windows, and a vyOS router. Going in, we had a plan to do something similar to what another team had done in the past, which was to essentially cut off the network and patch everything, the "Berkeley Turtle" strategy. We basically set up very restricted firewall rules to only allow access to the scored services and disallow connections from the red team. This worked pretty well since, as soon as we had a red teamer on a box, we could just cut them off and patch the box.
Honestly, a lot of us didn't really know what to do since we had zero experience with defending a network, let alone managing the various services such as Active Directory and DNS. Toward the end of the qualifier day, we got pretty hopeless as the red team started to double down on the vulnerabilities still present on our network. We basically just messed around in the last few hours of the competition because we felt like we had no chance of moving on.
Surprisingly enough, during the selection show, we found out that we had barely made the cut. The only new team to make it to regionals, with two members down, that was pretty big for us, especially being told that the Western Regionals was the most competitive region, apparently harder than nationals too.
Regionals¶
Now, honestly, we didn't learn our lesson from qualifiers by practicing for the competition. Our team doesn't have any training infrastructure, so some people just bought personal licenses to HTB and THM to practice. I had taken on the role of handling Active Directory, which I hated, and still do. Windows Server is essentially the core of the infrastructure of the competition since everything relies on the domain controller, so if it goes down, it's over for you. I spent a few hours a week just grinding out AD and hardening labs. I don't know how effective that was looking back at it, but I did learn a lot about AD. There's not much to say about our preparation for regionals, we were just happy to be there.
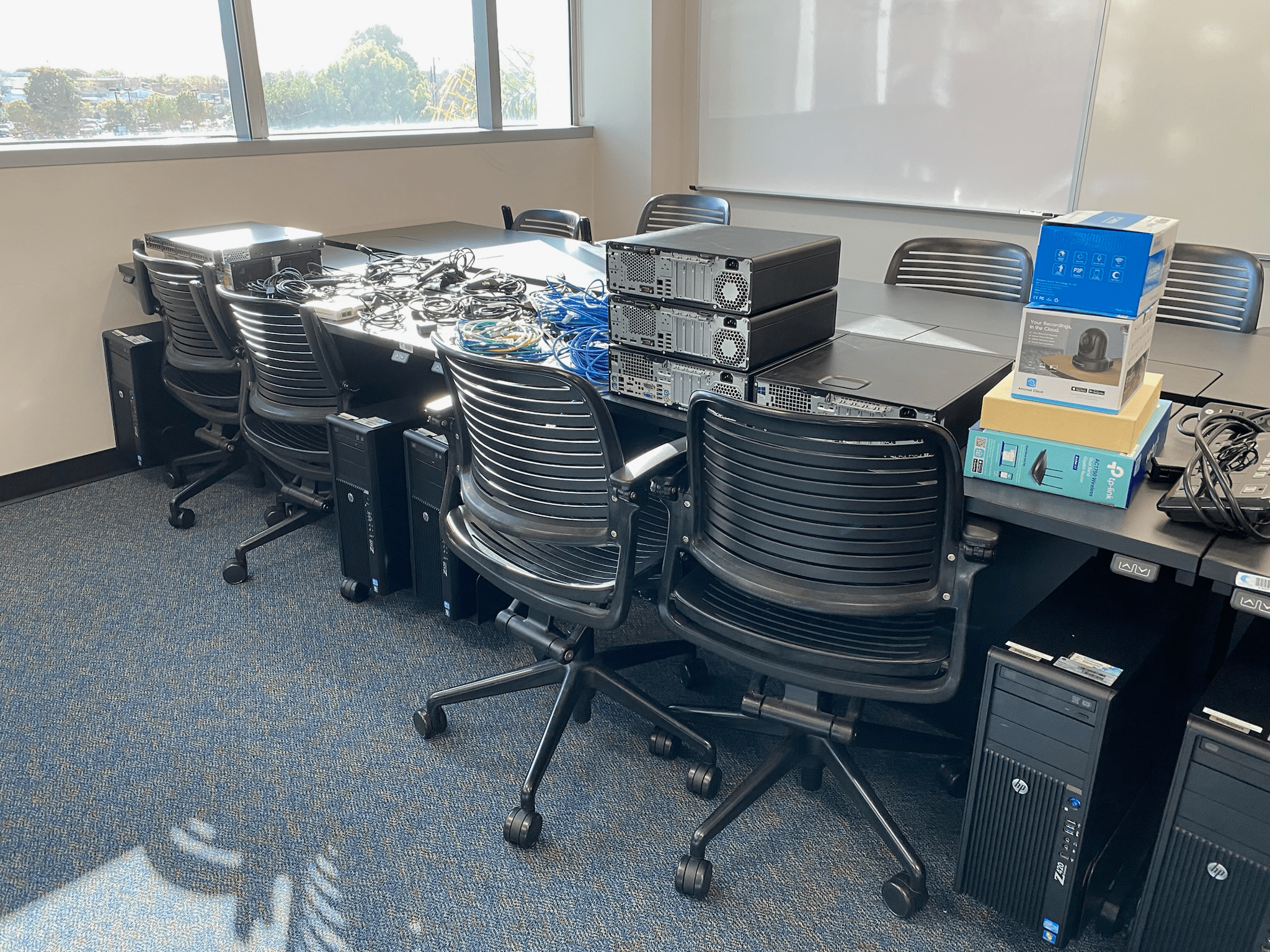
Regionals started off mostly without any technical issues. We were escorted to our rooms and had our phones taken. We had to deal with a lot of the same stuff as in the qualifiers, except now we had actual access to the hardware. We had a router, a switch, two IP cameras, two enterprise phone systems, two wireless access points, and a few Dell machines that acted as our servers. We actually missed a few items, mainly a NUC that was somewhat hidden in the corner of a table (that cost us a lot of points later on). The red team made a beeline for one of the IP cameras since we didn't reset the credentials on it in time. It wasn't a scored service, so we didn't really care, but we had some funny interactions with the red team since they could see what we were doing and listen in on conversations with the orange team (the people in character playing the roles of corporate/customers).
Compared to CPTC, the orange team and the admin team were much nicer to us. They were always checking in to see if we needed administrative support, and overall, they acted like they actually wanted to be there. I can only give props to the organizers for making the competition feel so interactive, not only with the tasks (like setting up a new service on Proxmox or configuring the access points) but also with the people.

At the end of day one, we learned we had actually placed around the top 4, which was a huge surprise to us. That really put us in a good mood for the next day. We wrapped everything up and set off to get some rest for the next day.
However, day two was a disaster for us. The red team had been in our network for a while, namely in our router, which they ended up bricking. With that, our entire network was down for hours, and we had to call the operations team for a box reset. It was so bad that operations spent a good hour and a half with us trying to recover the network. Similar to the qualifiers, we were essentially hopeless towards the end of the day, having no chance of recovering from the downtime.
Final Thoughts¶
We ended up placing pretty low, but we all had a lot of fun, even with what happened on day two. Our coach told us how they were in the coach room, watching the leaderboard, and seeing our team slowly fall during the outage. Overall, I loved the competition just for the interactions with the people there and the interactive network we had to manage against live threats.
I can't wait to go back next year and see how we do. We're planning to get more hands-on practice with applied cyber systems, setting up things like Game of Active Directory and other labs to practice on. Thank you everyone at CCDC for making the competition welcoming and fun. I hope to see you all next year.